WatchGuard Firewall Licensing: What You Need to Know
January 20, 2026 ·

WatchGuard licensing comes in multiple term lengths and three feature tiers. Check out the comparison chart below to find the best fit for your needs.
Firewall licensing is not a “one size fits all” decision. Every organisation’s network is different, and the level of protection you need depends on how you use your firewall, what you are protecting, and the potential impact of a security breach. Understanding these factors will help you make a balanced, cost‑effective choice.
VPN-Only or HA Secondary Unit:
If your firewall will be used mainly to VPN into a central unit that is already fully protected, or if it is a secondary device in a High Availability setup, the demands on it are lower. In these cases, the core security services of your main device are doing the heavy lifting, so Standard Support with centralised management and VPN capabilities is usually sufficient.
Core Enterprise Security Within a Tight Budget:
If you require essential enterprise-grade network security to shield against the majority of commodity cyberattacks, but are working with a tighter budget, then Basic Security licensing should be enough. This option covers foundation modules such as Antivirus, Intrusion Prevention and Spam Block. WatchGuard continuously records and updates protection against known threats, feeding that intelligence into your firewall to ensure that known attacks are blocked before they can enter your network.
Crucial Advanced Security Features:
The main leap in network protection comes with Total Security licensing. The first important benefit is ATP blocker. Cyber threats continue to evolve, and many major attacks now exploit vulnerabilities before patches are available. Data from 2024 shows that just over 50% of newly widespread threat vulnerabilities were zero-day exploits, meaning that attackers struck before the firewall vendors knew that the weaknesses existed. APT blocker assumes that every file or object attempting to enter the network could be malicious and uses advanced techniques such as sandboxing to block them from entering and dramatically reducing your exposure to modern ransomware and targeted attacks. Another key benefit of Total Security licensing is access to WatchGuard Threatsync XDR (Extended Detection and Response). Threatsync correlates security alerts from Firewalls, Access Points and Endpoint Security and correlates them into a unified incident log, highlighting events that truly matter and allowing automated or manual responses. Often different solutions can act in isolation which may allow gaps or blind spots that attackers can exploit. Threatsync brings all products together with centralised visibility allowing faster response-time and better protection. The Threatsync summary page includes graphs and incident data to provide a snapshot of incident activity.
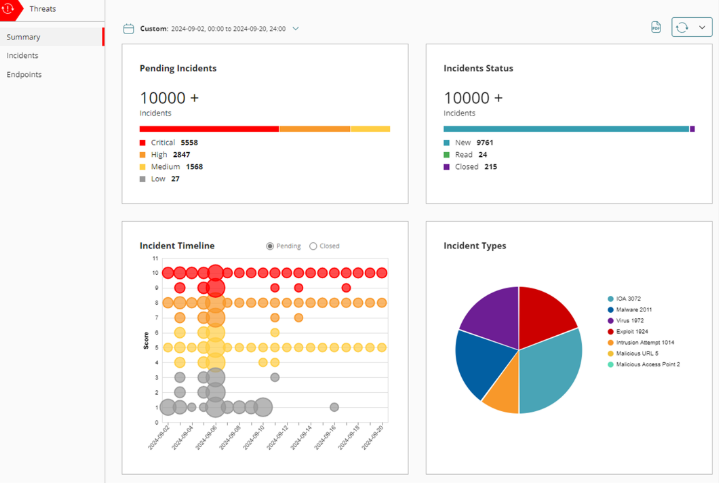
Our Recommendations:
Choose Total Security if…
- You use or plan to use WatchGuard Endpoint Security or Access Points alongside your Firewall
- You want unified visibility and automated threat response
- You cannot afford the downtime, cost, or reputational damage of a ransomware attack
- You want to meet certification standards like Cyber Essentials or ISO 27001
For these organisations, the advanced protections and XDR capabilities of Total Security are not optional — they are essential.
Choose Basic Security if…
- You’re on a tight budget
- You still need strong, essential enterprise security
- Your network environment is simple and lowrisk
Basic Security gives you everything required to defend against known threats without the cost of the advanced modules.
Choose Standard Support if…
- You only need VPN access
- You still need strong, essential enterprise security
- Your network environment is simple and lowrisk
This is the most costeffective option when advanced protection isn’t required.
| Included in Your Security Suite | Standard Support | Basic Security | Total Security |
|---|---|---|---|
| Stateful Firewall A stateful firewall tracks active connections to distinguish legitimate traffic from malicious attempts, providing enhanced security |
✓ | ✓ | ✓ |
| VPN A virtual private network (VPN) creates an encrypted, private connection over the public internet |
✓ | ✓ | ✓ |
| SD-WAN Software-Defined WAN (SD-WAN) automatically manages network traffic across multiple WAN connections according to defined policies |
✓ | ✓ | ✓ |
| Access Portal* A clientless VPN solution that enables safe remote access to essential web applications from anywhere |
✓ | ✓ | ✓ |
| Intrusion Prevention Service (IPS) IPS uses constantly updated signatures to monitor all major protocols, ensuring real-time protection against network threats |
✓ | ✓ | |
| Application Control Controls access to applications by granting, denying, or limiting permissions based on a user’s department, role, and the time of day, enhancing security and operational efficiency |
✓ | ✓ | |
| WebBlocker Automatically blocks known malicious sites and uses detailed content and URL filtering tools to prevent inappropriate content, save bandwidth, and boost productivity |
✓ | ✓ | |
| spamBlocker Provides real-time, continuous, and highly reliable protection from spam and phishing attempts |
✓ | ✓ | |
| Gateway AntiVirus Detects and blocks spyware, viruses, trojans, worms, rogueware, and complex threats, including the latest variants of known viruses |
✓ | ✓ | |
| Reputation Enabled Defense Cloud-based web reputation service that aggregates data from multiple feeds to provide real-time protection from malicious sites and botnets |
✓ | ✓ | |
| Network Discovery Generates a visual map of all nodes on your network, ensuring only authorized devices are connected while detecting all open ports and protocols |
✓ | ✓ | |
| APT Blocker Detects and stops the most sophisticated attacks, including ransomware, zero-day threats, and other advanced malware Learn more |
✓ | ||
| DNSWatch Blocks malicious DNS requests, redirects users to a secure, informative page, and promotes best security practices to prevent phishing attacks and reduce malware infections Learn more |
✓ | ||
| IntelligentAV** Automates malware discovery and classify current and future threats in mere seconds with AI-powered intelligence Learn more |
✓ | ||
| ThreatSync (XDR) AI-driven threat detection and response for advanced threats, including ransomware, supply chain, and vulnerability-based attacks Learn more |
✓ | ||
| EDR Core Continuous AI-powered endpoint monitoring for suspicious activity that detects threats in real time, and enables rapid investigation and response Learn more |
✓ | ||
| WatchGuard Cloud Securely stores firewall logs and reports for easy access, analysis, and compliance |
✓ | ||
| Log Data Retention | 90 Days | 365 Days | |
| Report Data Retention | 1 Day | 30 Days | |
| Support | Standard (24x7) | Standard (24x7) | Gold (24x7) |
*Not available on Firebox T115-W, T20/T20-W, T25/T25-W, or T35-R. Total Security Suite required for M270, M370, M470, M570, M670, FireboxV and Firebox Cloud.
*Not available on Firebox T115-W, T20/T20-W, T25/T25-W, or T35-R<< /p>
